How JavaScript Uses Hashing
Hashing is one of the most powerful tools in computing, especially in areas like data security, data storage, and quick data retrieval. In JavaScript, hashing plays a significant role in both the backend and frontend, powering structures like "map" objects and supporting secure applications through libraries like "crypto".
What is Hashing and What is it Used For
Hashing is a process that converts an input (or ‘message’) into a fixed-length string of bytes, typically using a mathematical function called a hash function. This result is known as the hash value, digest, or simply the hash.
A key feature of hashing is that:
- The same input always gives the same output.
- It’s one-way, you cannot reverse the hash back to the original data.
- Even a tiny change in the input drastically changes the output (called the avalanche effect).
Common Uses of Hashing:
- Password Storage: Instead of storing passwords in plain text, we store their hash. When a user logs in, we hash their entered password and compare it to the stored hash.
- Version Control: Systems like Git use hashing (e.g., SHA-1) to identify file versions.
- Data Integrity: You can compare file hashes to ensure that two files are identical and have not been altered.
- Cryptocurrencies: Bitcoin relies on hashing to secure transactions.
- Efficient Lookup: Hashing is used in creating hash tables, enabling near-instantaneous data retrieval.
What is a Hash Table and Why is it Useful
A hash table is a data structure that maps keys to values for efficient lookup. It uses a hash function to convert the key (often a string) into an index in an internal array where the value is stored.
Example:
Here, the names are keys, and a hash function internally determines where in memory the phone numbers will be stored.
Benefits of Hash Tables:
- Fast Lookup: Time complexity is O(1) for average-case scenarios. Meaning the time taken to complete a operation remains the same regardless of how musch data is in the structure.
- Efficient Insertions and Deletions.
- Scalable for large datasets.
- Widely Used: Found in many programming languages and databases.
Hashing vs Encryption
Hashing is for verification, encryption is for secrecy. The bullet points below will make things easier to understand.
Hashing Features:
Hashing Features:
- Direction: One-way.
- Purpose: Verification, integrity, quick lookup.
- Output: Fixed-length digest.
- Reversible: No
- Example Use: Password storage.
Encryption Features:
- Direction: Two-way (encrypt and decrypt).
- Purpose: Data confidentiality.
- Output: Encrypted text (ciphertext).
- Reversible: Yes (with the key).
- Example Use: Sending secure messages.
JavaScript’s Map Objects and Hash Tables
JavaScript has a built-in "map" object introduced in ES6, which internally uses hash tables for quick lookups.
What is a "Map" in javascript?
A "map" is a collection of key-value pairs where:
- Keys can be of any type (not just strings or symbols).
- Insertion order is preserved.
- Optimized for frequent additions and deletions.
Example:
Object Features:
- Key types: Strings or Symbols only.
- Key ordering: Unordered.
- Performance: Slower for frequent ops.
- Underlying Data: Not necessarily hashed.
Map Features:
- Key types: Any value (including objects).
- Key ordering: Ordered.
- Performance: Optimized for frequent use.
- Underlying Data: Often implemented with hash table.
In both cases, hashing may be used under the hood, especially in "map", to index keys efficiently.
How Hashing Improves Security in JavaScript
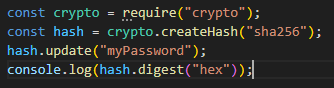
JavaScript (especially in Node.js) uses the "crypto" module for cryptographic functions like hashing.
Example:
- Passwords are never stored directly, only their hash is saved.
- Data integrity can be verified using checksums.
- Hashing with salting prevents rainbow table attacks (eg, precomputed hash tables).
Popular libraries:
- bcrypt: for salted password hashing.
- crypto: for hashing algorithms like SHA256, SHA512, etc.



Comments
Post a Comment